Backup Compliance Tips to Turn Legal Requirements Into Business Advantages
 John Turner
John Turner
 John Turner
John Turner
How you manage your backup data matters just as much as having backups in the first place.
Your backup files are copies of all your live data, which means they fall under the same privacy laws, security regulations, and industry standards.
In this blog post, I’ll walk you through everything you need to know about backup compliance.
You’ll learn:
- What backup compliance means and how it applies to your business
- Key legal requirements from GDPR, CCPA, HIPAA, and other major regulations
- Essential backup compliance measures like encryption and access controls
- How to create compliant data retention and deletion policies
- Practical steps to test, document, and audit your backup systems
- A complete compliance checklist you can implement immediately
Table of Contents
What Is Backup Compliance?
Backup compliance means your backup strategy follows all the legal and industry rules that apply to your data.
When you create a backup, you’re making an exact copy of your live website data. If your live site contains personal information, financial records, or health data, then your backups contain that same sensitive information.
The law doesn’t care whether data is “live” or “backed up.” Sensitive data is sensitive data, regardless of where it sits.
This means your backups must follow the same privacy laws, security standards, and industry regulations as your main website. You can’t just dump backup files anywhere and call it done.
Backup compliance covers the entire lifecycle of your backup data. From the moment you create a backup file to the day you permanently delete it, every step needs to follow the rules.
That includes:
- How you create backups
- Where you store them
- Who can access them
- How long you keep them
- How you securely delete them when they’re no longer needed
Key Aspects of Backup Compliance
Backup compliance is a collection of requirements that work together to protect your data and keep you legally compliant. Understanding these key aspects will help you build a backup strategy that covers all the bases.
Regulatory Compliance
Your backup strategy must follow laws based on where your users are located, not just where your business is.
If you have visitors from Europe, GDPR applies to your backups. Customers from California? CCPA rules kick in. The location of your users determines which regulations you need to follow.
Don’t worry, I’ll explain these legal requirements in depth later in this tutorial.
Data Security
Two things matter most here: encryption and access controls.
Your backup data should be encrypted both when it’s traveling to storage (in transit) and when it’s sitting in storage (at rest). Without encryption, your backup files are readable by anyone who accesses them.
Access controls mean following the principle of least privilege. Only the people who absolutely need access to backup files should have it. Everyone else should be locked out.
Data Retention
You need to keep backups long enough to meet business needs. However, you also need to delete them eventually to respect privacy rights.
A formal retention policy isn’t optional. You need written rules that specify exactly how long different types of backups are kept and when they get deleted.
RTO and RPO
Recovery Time Objective (RTO) is how fast you need to get back online after a disaster. Recovery Point Objective (RPO) is how much data loss you can accept.
Both numbers affect your compliance because they determine how quickly you can restore services and how much customer data might be at risk during an outage.
Testing and Validation
You should regularly test your backups by actually restoring them. This proves your backup system works and that you can meet your RTO and RPO commitments.
Document every test. If you get audited, you’ll need proof that your backup system actually works as intended.
Documentation
Everything needs to be documented. Your backup policies, test results, retention schedules, security measures—all of it.
If auditors come calling, they’ll want to see evidence that you’re actually following the rules, not just claiming that you are.
Cloud Storage
Using a cloud provider doesn’t automatically make you compliant. You’re still responsible for configuring everything correctly.
That means setting up encryption, choosing the right data residency options, and picking a provider with the proper security certifications for your industry.
The cloud provider handles the infrastructure, but the compliance responsibility is still yours.
What Data Regulations Should You Know?
Different regulations have different rules, but they all affect how you handle backup data. Here are the key ones you should know about for your business:
- GDPR: European privacy law with “right to be forgotten” requirements
- CCPA/CPRA: California privacy laws with data deletion rights
- HIPAA: US healthcare data protection with strict encryption standards
- PCI DSS: Credit card data security requirements
- PIPEDA: Canadian privacy law with security safeguards
- NIS2 Directive: EU cybersecurity requirements
- DORA: EU financial services operational resilience standards
GDPR
The General Data Protection Regulation (GDPR) is Europe’s comprehensive privacy law. It applies to any business that processes personal data of EU residents, regardless of where your company is located.
Two things matter most for your backups: the “right to erasure” (also called the “right to be forgotten”) and data residency requirements.
When someone requests that you delete their personal data, you can’t just delete their data from your live website and call it done. You need a documented process for handling their personal data in all your backup files, too.
You need a reasonable retention policy that automatically deletes old backups containing their data within a specific timeframe. You can’t keep personal data in backups indefinitely just because it’s convenient.
The other part, data residency, gets tricky with backups.
The GDPR generally requires EU personal data to stay within the EU or in countries that the European Commission has deemed to have adequate data protection. This means you need to know exactly where your backup files are physically stored and ensure those locations meet GDPR requirements.
CCPA/CPRA
The California Consumer Privacy Act (CCPA) and its successor, the California Privacy Rights Act (CPRA), give California residents specific rights over their personal information. These laws apply if you collect personal information from California residents.
Like GDPR, this affects your backup retention policy. When someone requests deletion, you need a clear process for handling their request across all your data storage, including backups.
CCPA allows businesses to keep personal information in backups for “internal uses reasonably aligned with consumer expectations.” However, you still need clear policies about how long backup data is retained and when it gets permanently deleted.
The CPRA introduced the concept of “sensitive personal information,” which includes precise geolocation data, racial or ethnic origin, religious beliefs, and biometric identifiers.
This data has stricter handling requirements that extend to backup storage. You need enhanced security measures for backup files containing sensitive personal information, and consumers have additional rights to limit how this data is used.
HIPAA
The Health Insurance Portability and Accountability Act (HIPAA) protects health information in the United States. If your website handles any protected health information (PHI) like patient records, health insurance information, or even basic health-related data, HIPAA compliance is mandatory.
HIPAA’s backup requirements are particularly strict. All PHI in backup files must be encrypted using FIPS 140-2 validated encryption. You also need logging to track who accesses backup data and when.
Business Associate Agreements (BAAs) are required with any third-party vendor who might have access to your backup data. This includes your cloud storage provider, backup service vendor, and even your hosting company if they could potentially access your backup files.
The regulation also requires specific data retention and disposal procedures. You need documented policies for how long backup data containing PHI is kept and secure deletion procedures.
PCI DSS
The Payment Card Industry Data Security Standard (PCI DSS) applies if you store, process, or transmit credit card information. Even if you use a payment processor, PCI DSS requirements often extend to backup data that might contain cardholder information.
Any backup files containing credit card numbers, expiration dates, or cardholder names must be encrypted with strong cryptography. The standard requires AES encryption with a minimum key length of 128 bits.
PCI DSS also mandates secure key management for backup encryption. Encryption keys must be stored separately from encrypted backup data and protected with strong access controls.
You can only keep cardholder data as long as it’s needed for business or legal purposes. Your backup retention policy must align with these requirements and include secure deletion procedures.
PIPEDA
Canada’s Personal Information Protection and Electronic Documents Act (PIPEDA) governs how private sector organizations collect, use, and disclose personal information during commercial activities.
PIPEDA requires “appropriate security safeguards” for personal information, which extends to backup data. The law doesn’t specify exact technical requirements, but it does require that security measures be appropriate for the sensitivity of the information.
For backup compliance, this means implementing reasonable encryption, access controls, and retention policies based on the type of personal information you’re protecting.
The law also includes breach notification requirements. If backup data containing personal information is compromised, you may need to notify both the Privacy Commissioner and affected individuals.
NIS2 Directive
The updated Network and Information Security Directive (NIS2) significantly expands cybersecurity requirements for websites across the European Union.
NIS2 specifically addresses business continuity and disaster recovery. You have to use appropriate backup and recovery systems as part of your overall cybersecurity risk management.
The regulation requires regular testing of backup systems and incident response procedures. You need documented evidence that your backup and recovery processes work and can meet your business continuity objectives.
Significant cyber incidents must be reported to authorities within 24 hours, which means your site needs to support rapid incident response.
DORA
The Digital Operational Resilience Act (DORA) targets financial services in the European Union, requiring financial entities to maintain operational resilience against ICT (Information and Communication Technology) risks.
For this regulation, financial institutions must demonstrate that they can maintain critical functions during and after operational disruptions.
The regulation requires regular testing of backup systems through various scenarios, including cyber attacks and system failures. These tests must be documented and reported to supervisory authorities.
Third-party risk management under DORA also affects backup compliance. If you use cloud storage or backup service providers, you need to ensure they meet DORA’s standards.
What Are the Benefits of Keeping Your Backups Compliant?
I just threw a lot of laws at you, but backup compliance isn’t just about avoiding trouble. Done right, it makes your business stronger.
Customers care about how you handle their data. When they know you take data protection seriously (including in your backups), they’re more likely to trust you with their business.
This becomes a competitive advantage. While your competitors are scrambling to fix compliance problems after the fact, you can focus on growing your business.
Plus, regulatory penalties can be massive. GDPR fines can reach 4% of your annual global revenue. HIPAA violations can cost hundreds of thousands of dollars per incident.
A compliant backup strategy helps you avoid these financial hits by keeping you on the right side of the law from day one.
When disaster strikes, you’ll recover faster because your systems are documented, your processes are proven, and your team knows exactly what to do.
Working through compliance requirements forces you to really understand what data you have and where it lives.
This improved visibility reduces risk across your entire business, not just in your backup systems. You’ll spot potential problems earlier and make better decisions about data handling.
Backup Compliance Checklist
Here’s your practical roadmap to backup compliance.
Know Your Data
Start with a complete audit of what data you collect and store.
Create a data inventory that documents every type of information your website handles. This includes obvious things like user registration data and contact form submissions, but also less obvious data like server logs, error logs, cached content, and temporary files.
Classify everything by sensitivity level. Personal information, financial data, and health records need different levels of protection.
Use categories like “public,” “internal,” “confidential,” and “restricted” to organize your data classification.
Map out where this data lives in your system. Check your database tables, uploaded file directories, log files, cached data, session storage, and any third-party integrations.
Document data flows to understand how information moves through your system. Personal data submitted through a contact form might end up in your database, email system, CRM, and backup files. You need to track all these touchpoints.
Pay special attention to data retention requirements for different types of information. Some data might need to be kept for legal reasons (like financial records), while other data should be deleted as soon as it’s no longer needed (like temporary session data).
Define Your Retention Policy
Write down your Recovery Time Objective and Recovery Point Objective. These numbers drive everything else in your backup strategy.
Your RTO should reflect real business needs. If your e-commerce site being down for four hours costs you $10,000 in lost sales, your RTO needs to be much shorter than four hours. Be realistic about what you can achieve with your current resources.
Your RPO determines how often you need to create backups. If you can only afford to lose one hour of data, you need backups at least every hour.
Factor in the time it takes to restore a backup when calculating your RPO.
Create a formal retention schedule that specifies exactly how long different types of backups are kept. Your retention periods should balance compliance requirements, storage costs, and recovery needs.
Use Access Controls
Define access controls and approval processes for backups.
Who can create backups? Who can access backup files? Who can restore a backup? What approval is needed for each type of access?
A tool like Duplicator can make these rules specific. It’s a backup plugin that comes with customizable access controls. This helps you decide who can access, create, or restore backups.
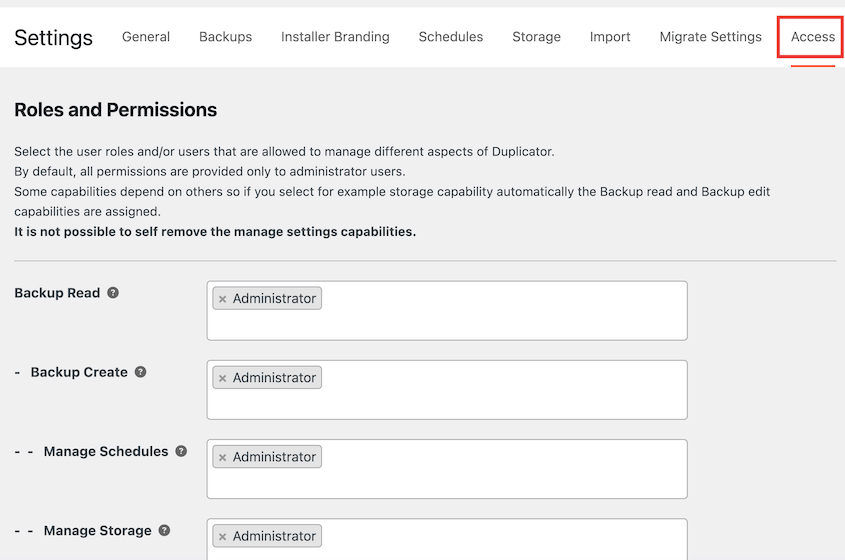
Include incident response procedures in your policy.
What happens if backup data is compromised? Who gets notified? What steps need to be taken to contain the breach and notify affected parties?
With Duplicator, you can automate retention policies. It’ll automatically delete old backups according to your specified schedule so you don’t have to manage this manually.
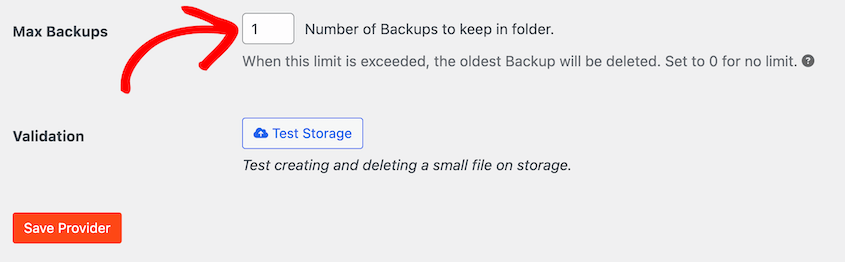
Choose Compliant Storage
Pick a storage provider based on their security certifications and compliance capabilities, not just price.
Make sure you can keep data in the right geographic locations for your compliance requirements. Some providers offer region-specific storage options, while others may replicate data across multiple countries without clear controls.
Verify that your provider offers the encryption and access control features you need. Look for AES-256 encryption, key management services, and integration with identity and access management systems.
Review the provider’s incident response and breach notification procedures. How quickly will they notify you if there’s a security incident? What information will they provide? How will they support your own breach notification obligations?
Duplicator integrates with over a dozen secure cloud storage providers, including options that meet various compliance requirements.
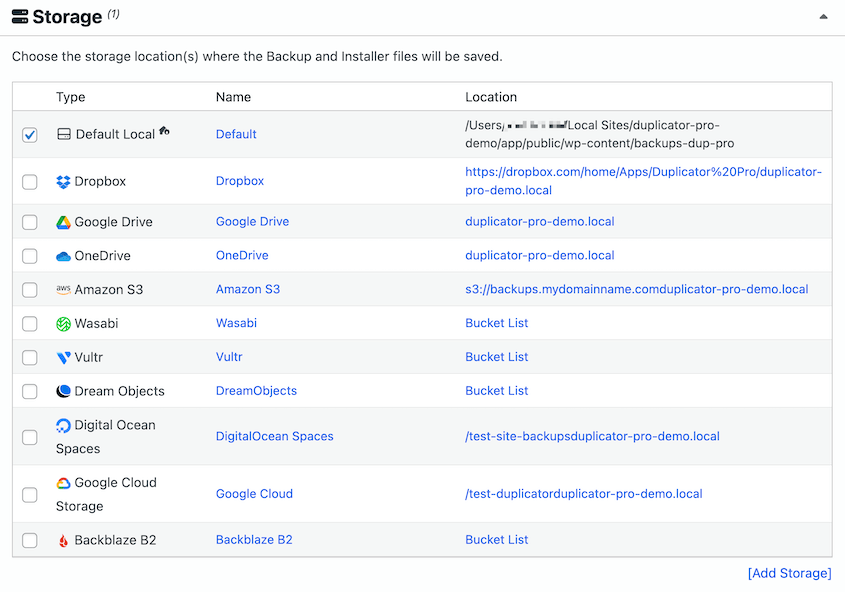
Secure Your Backups
Turn on encryption for data in transit and at rest. Use strong encryption standards—AES-256 is the current best practice.
Duplicator Pro can encrypt all backup files with AES-256 encryption, both during transfer and storage, removing the guesswork.
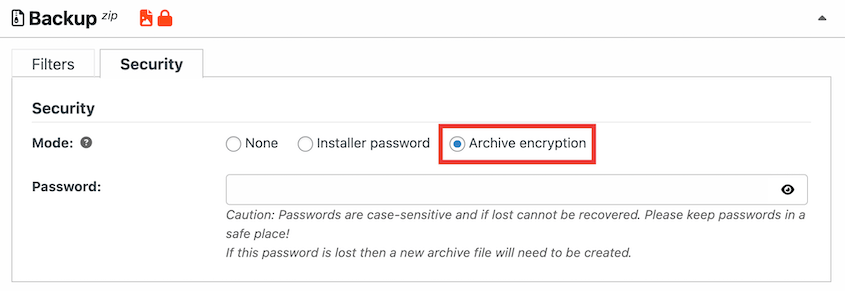
Encryption keys should be stored separately from encrypted backup data and protected with strong access controls. Consider using a dedicated key management service or hardware security modules for sensitive data.
Set up comprehensive access controls using Identity and Access Management (IAM) tools. Implement the principle of least privilege—users should only have access to the specific backup data they need.
Set up monitoring and alerting for backup access. You should receive notifications when backup data is accessed, when new backups are created, and when any configuration changes are made to your backup systems.
If you use Duplicator to manage backups, you’ll get automatic backup failure notifications.
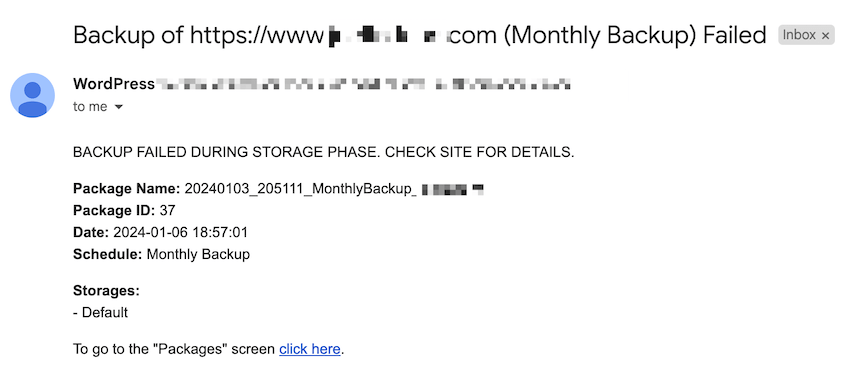
Plus, you can set up regular email summaries sent straight to your inbox. These include all your new backups, storage locations, and schedules.

Duplicator can send you email summaries every day, week, or month. You’ll know exacly when your sites are backed up!
Test Backups Regularly
Schedule restoration tests at least quarterly. More often is better, especially for critical systems.
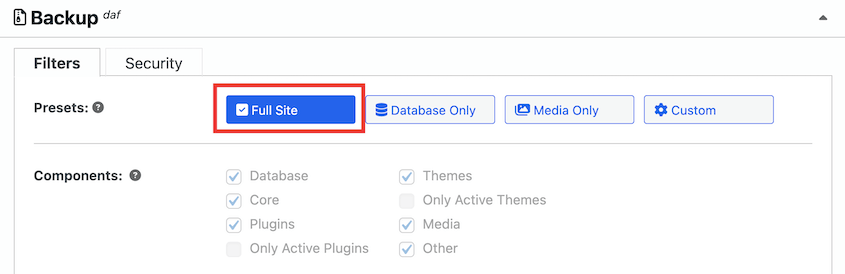
Create a formal testing schedule that covers different types of restoration scenarios. Test full site restores, partial restores, database-only restores, and file-only restores.
Each type of restore might uncover different issues.
Don’t test restores on your live website—use a staging server or development environment that has the same operating system, web server software, and database versions.
If you need to create a new staging site, set one up locally with LocalWP or XAMPP. Create a full-site backup of your website with Duplicator.
Download the backup archive file. Once you finish creating the local staging site, import the backup. Duplicator will automatically set up a copy of your data in the staging area for you to test.
Measure and document restore performance against your RTO and RPO objectives. If restores consistently take longer than your RTO allows, you need to improve your backup strategy or adjust your objectives.
Frequently Asked Questions (FAQs)
Do all websites need to worry about backup compliance?
Yes, if you collect any personal information from visitors. Even simple contact forms, email signups, or basic analytics tracking mean you’re handling personal data, and compliance rules apply to how you back up and store that information.
How long should I keep my website backups?
It depends on your business needs and regulatory requirements, which is exactly why you need a written retention policy. Start by checking what regulations apply to your business and data, then write down specific retention periods for different types of backups and stick to those rules.
How do I handle a “right to be forgotten” request from a user?
First, remove their data from your live website immediately. For backups, follow your retention policy—you don’t have to scrub old backup files manually, just let those backups expire and get deleted according to your normal retention schedule.
Where is the safest place to store my backups?
The safest place to store backups is on an off-site, encrypted, and reputable cloud provider that has proper security certifications. Follow the 3-2-1 rule: keep 3 copies of your data on 2 different types of storage media, with 1 copy stored off-site.
Make Compliance a Cornerstone of Your Backup Strategy
Backup compliance is about being intentional and organized with how you protect your most valuable business asset: your data.
When you build compliance into your backup strategy from the beginning, you transform backups from a simple technical task into a responsible business process.
You’ll sleep better knowing your data is protected. Your customers will trust you more. And when disaster strikes, you’ll recover faster and more completely.
But here’s the reality: managing all these compliance requirements manually is time-consuming and error-prone. You need tools that can automate the heavy lifting while keeping you compliant.
Duplicator Pro can handle the technical complexity of compliance automatically. It has AES-256 encryption, automated retention policies, scheduled testing, and seamless integration with a dozen secure cloud storage providers.
Stop worrying about whether your backups meet compliance requirements. Let Duplicator Pro handle the technical details so you can focus on growing your business with confidence.
While you’re here, I think you’ll like these other hand-picked resources:

![[New Plugin] Activity Log: Track Every Change, Login, and Action on Your WordPress Site](https://duplicator.com/wp-content/uploads/2026/02/Announcement-Activity-Log.jpg)