WordPress Firewalls: Your Site’s First Line of Defense
 John Turner
John Turner
 John Turner
John Turner
If you’ve ever checked your WordPress site’s logs, you know the truth: your website is under constant attack.
Right now, automated bots are scanning the internet, probing millions of WordPress sites for weaknesses. They don’t care if you’re a small business or a personal blogger – they’re looking for any vulnerability they can exploit.
Running a WordPress site makes you a target, plain and simple. Since WordPress powers over 40% of all websites, attackers focus their efforts on where they’ll get the most return.
Your site is in their crosshairs, whether you realize it or not.
This is exactly why a firewall for WordPress isn’t optional – it’s your digital bouncer, standing at the door and turning away suspicious visitors before they can cause trouble.
In this guide, I’ll break down what a WordPress firewall actually does and how to set one up.
What Is a Firewall?
Think of a firewall as your website’s security guard. It stands between your WordPress site and the rest of the internet, checking everyone who wants to come in.
At its core, a website firewall is a filtering system. It examines the data trying to reach your site and makes split-second decisions: “Is this legitimate traffic or a potential threat?”
Every time someone (or something) tries to access your site, they send what’s called an HTTP request. These requests contain data packets with information about who they are, what they want, and how they’re asking for it.
Your firewall inspects these packets, looking for suspicious patterns.
When the firewall spots something fishy – like a request trying to access admin areas through unusual means, repeated login attempts from the same source, or traffic matching known attack signatures – it blocks it before it reaches your WordPress site.
Your computer likely has a firewall, your home router probably has one too, and large organizations use network firewalls to protect entire systems. The principle is the same: filter out the bad stuff before it can do harm.
Does WordPress Have a Firewall?
The short answer? No, WordPress doesn’t come with a built-in firewall.
WordPress core includes some basic security measures – it has secure authentication processes and data sanitization to prevent certain types of attacks. The WordPress team also works hard to patch vulnerabilities quickly when they’re discovered.
But when it comes to actively filtering malicious traffic before it reaches your site? That’s not included out of the box.
This gap exists by design. WordPress is a content management system, not a security suite. It’s built to be extended with the exact functionality you need, rather than bundling everything possible into the core software.
This is where plugins and server configurations come in. You’ll need to add firewall functionality to your WordPress site, either through a security plugin that includes WAF (Web Application Firewall) features or through server-level protections.
Why Your WordPress Site Should Have a Firewall
Bots and crawlers constantly scan the internet for vulnerable WordPress installations. Your firewall is what keeps them from hammering your WordPress login page or probing for outdated plugins with known security holes.
Beyond brute force attempts, a good firewall blocks traffic from known malicious IP addresses. It also recognizes common WordPress attacks like SQL injection or cross-site scripting (XSS).
These attacks try to inject harmful code into your site – code that could steal data, redirect visitors, or completely take over your website.
There’s also a performance benefit. When bad traffic gets filtered out before it fully processes through your WordPress installation, your server resources stay focused on legitimate visitors. This often results in better speed and responsiveness for actual users.
The consequences of skipping this protection can be severe. A compromised WordPress site might be defaced, have malware injected, or even be used to attack other sites. Once that happens, you’re looking at potential downtime, data loss, and the painstaking work of malware removal.
Your reputation takes a hit too. Visitors may see browser warnings about your site being unsafe, and Google might flag or even delist your site from search results. Some hosting companies will even suspend accounts that become security risks to other customers.
Different Types of Firewalls
Not all WordPress firewalls work the same way. Understanding the differences helps you choose the right protection for your site.
Web Application Firewalls (WAFs)
These are the most relevant for WordPress users, as they’re specifically designed to protect web applications like WordPress, Joomla, or Drupal.
WAFs filter HTTP traffic (the requests coming to your website) looking for suspicious patterns or known attack signatures. There are two different types.
Endpoint WAFs run directly on your server, usually as a WordPress plugin. They check traffic after it reaches your server, but before WordPress fully processes it.
I like these because they’re easier to set up and often provide detailed logs right in your WordPress dashboard. They’re examining traffic that’s already reached your server, though, which means they can’t prevent server overload from massive attacks.
Cloud-based WAFs work differently. They act as a proxy between visitors and your website – all traffic passes through their network before reaching your server.
The advantage here is they can block large-scale attacks before they hit your server, preventing performance issues. The trade-off is they typically require DNS changes and might add a tiny bit of latency (though usually not noticeable).
Server-Level Firewalls
These work on the operating system level on your web server. They’re looking at network traffic more generally, filtering based on IP addresses, ports, and protocols.
If you’re on shared hosting, your provider probably has server-level firewalls in place, but you likely can’t configure them yourself.
Server firewalls provide broader protection, but aren’t as WordPress-specific as WAFs. They’re great at blocking suspicious connections, but are less equipped to identify application-specific attacks.
Network Firewalls
These exist at network boundaries and typically protect entire networks rather than individual websites.
As a WordPress site owner, you generally won’t directly manage these unless you’re running an enterprise-level setup. Your hosting company almost certainly uses them as part of its infrastructure.
How to Install a Firewall in WordPress
For most site owners, the simplest approach is using a security plugin that includes WAF functionality. Some of the best WordPress firewall plugins include:
- Wordfence Security
- Sucuri Security
- Solid Security (formerly iThemes Security)
- All-In-One WP Security & Firewall
- Jetpack Security
- Bulletproof Security
- Security Ninja
- Shield Security
If you’re on a tight budget, consider a free WordPress firewall solution to start with, then upgrade as your site grows.
For plugin-based (endpoint) WAFs, the configuration typically involves:
- Running the plugin’s setup wizard if offered
- Enabling the firewall component (some plugins have this off by default)
- Choosing your protection level
- Configuring WordPress firewall settings to match your site’s specific needs
- Allowing the plugin to modify your .htaccess file (on Apache servers) or providing nginx configuration (on nginx servers)
The last step is important – it allows the firewall code to run earlier in the page loading process, before WordPress itself loads. This makes it more effective against certain attacks.
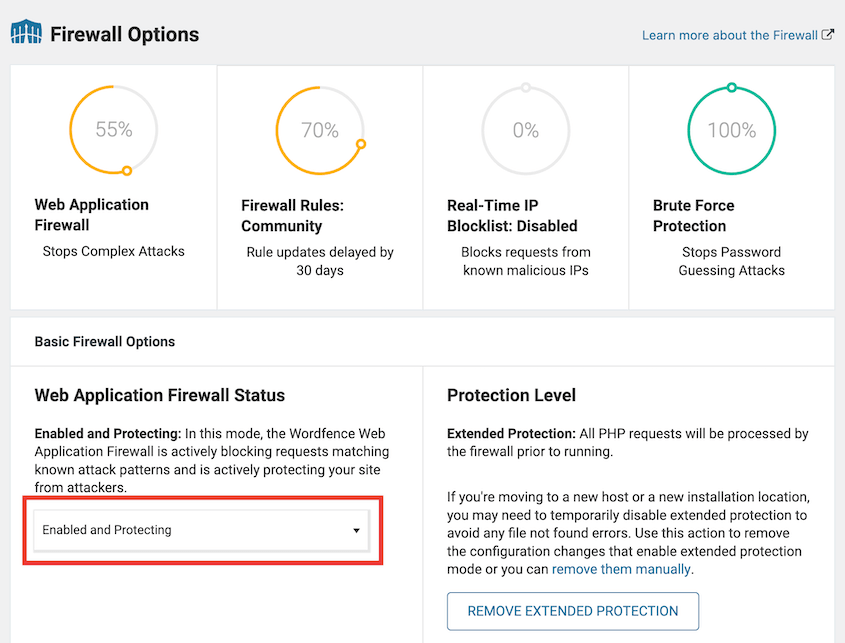
For cloud-based WAFs like Sucuri’s, you’ll need to:
- Sign up for their service
- Follow their instructions to change your DNS records
- Point your domain to their proxy servers, which will filter traffic before sending it to your actual host
The first time I set up a firewall, I was nervous about breaking my site. But the process has become much more user-friendly over the years. Most plugin interfaces walk you through each step.
If you’re not comfortable making these changes yourself, consider hiring a developer for an hour or two to set things up properly. The investment is well worth the protection you’ll receive.
Potential Issues with WordPress Firewalls
While firewalls are essential, they’re not without their challenges. Being aware of these potential pitfalls helps you address them quickly if they arise.
False Positives
This is probably the most common headache – when your firewall mistakenly blocks legitimate traffic.
Common scenarios include:
- Legitimate API calls from services you use getting blocked
- Search engine bots being mistaken for scrapers
- Your own access getting blocked if you trip a rule
Most firewall plugins have a whitelist feature for this reason. If you find certain services or users being blocked incorrectly, you can add them to this safe list.
Performance Impact
Firewalls add processing overhead since they examine every request. While usually minimal, this can add up.
Endpoint (plugin) firewalls use your server’s resources and can slow down page loading if not optimized. Cloud-based firewalls add a bit of latency as traffic routes through their servers first.
If your site feels slower after installing a firewall, you might need to adjust settings or upgrade to a more efficient solution.
Plugin Conflicts
Like any plugin, security tools can sometimes clash with other parts of your WordPress setup.
Here’s what could happen:
- Custom code or themes might trigger false positives
- Other security plugins might conflict with your firewall
- Caching plugins sometimes need special configuration to work with firewalls
If you notice strange behavior after installing a firewall, try temporarily deactivating other plugins one by one to identify any conflicts.
Configuration Complexity
Getting the settings just right can be tricky. Set rules too strict, and you block legitimate users. Too loose, and you leave vulnerabilities.
This is especially true if you have custom setups like:
- Membership sites with restricted content
- E-commerce functionality
- Custom AJAX requests
- Third-party integrations
- Modified login URL for additional security
Start with default settings, then gradually adjust as you learn what works for your specific site.
Cost Considerations
While free options exist, extra protection often requires paid subscriptions. You might need to upgrade for these features:
- Advanced rule sets
- Real-time updates against new threats
- Premium support
- DDoS protection
- Country blocking
These costs are an investment in security, but they should be factored into your website budget.
Not a Complete Security Solution
Perhaps the biggest issue is the false sense of security a firewall might give you. It’s a critical layer, but not your only defense.
A firewall won’t help if:
- You use weak admin passwords
- You don’t keep WordPress core, themes, and plugins updated
- You or your team fall for phishing attacks
- Malware somehow gets uploaded through legitimate channels
This is why a multi-layered approach (including reliable WordPress backups) remains essential.
How to Know If Your Firewall is Failing
A firewall that isn’t doing its job can give you a dangerous false sense of security. Here are warning signs that your protection might be compromised.
Check Your Logs Regularly
Most firewall plugins provide activity logs showing what they’ve blocked. Make this part of your regular site maintenance.
Answer these questions:
- Are attacks being detected AND blocked?
- Do you see patterns of malicious requests getting through?
- Has there been a sudden drop in blocked attempts? (This might mean the firewall isn’t catching things)
I make a habit of scanning these logs weekly. Once you know your site’s normal pattern, anomalies become easier to spot.
Unusual Login Activity
A spike in failed login attempts that aren’t being blocked is a major red flag. Even worse is if you notice successful logins from unfamiliar locations or at odd hours.
Set up login notifications if your firewall or security plugin offers this feature. Getting an email when someone logs in provides an early warning system.
Unexplained Performance Issues
If your site suddenly slows down without a corresponding increase in legitimate traffic, your firewall might be struggling or letting through attack traffic that’s bogging down your server.
Check your hosting metrics alongside your firewall stats. A performance drop combined with increased resource usage could indicate your site is handling attacks your firewall should be blocking.
Hosting Provider Alerts
Your hosting company often has additional monitoring systems. If they contact you about suspicious activity originating from your site, take it seriously.
These notifications usually mean something has already bypassed your security and compromised your site.
Visible Site Changes
The most obvious sign of firewall failure is finding unexpected changes to your site, like:
- Defacement (changes to your content)
- New admin users you didn’t create
- Suspicious files in your directories
- Redirects to other websites
- Strange code injected into your pages
By this point, you’re dealing with cleanup rather than prevention.
External Security Scans
Running occasional external security scans can catch issues your internal tools miss. A good vulnerability scanner can identify potential weak points before they’re exploited.
Services like Sucuri SiteCheck or Google’s Security Issues report in Search Console can identify vulnerabilities or active infections that your firewall should have prevented.
Regular malware scans should be part of your security routine.
If your firewall is failing, don’t just tweak settings and hope for the best. Consider switching to a different firewall service entirely.
And remember – this is exactly why keeping regular, secure backups with a tool like Duplicator is non-negotiable for any WordPress site owner. If hackers come through your firewall, you’ll want to quickly restore your site to a clean state.
Frequently Asked Questions (FAQs)
Do I need a firewall for my website?
Yes, if you have a WordPress website, you should have a firewall. Your site is being probed by automated attacks constantly, regardless of its size or popularity. A firewall is as basic and necessary as having locks on your doors – it’s fundamental protection, not an optional extra.
What is the best free security plugin for WordPress?
Wordfence Security is a free security plugin with solid firewall protection. If you’re looking for a low-cost security tool, I’d highly recommend it.
Does WordPress have built in security?
WordPress core does include some security features like regular updates. However, it doesn’t have a built-in firewall to actively filter and block malicious traffic. That critical security layer needs to be added separately through plugins or server configurations.
Is a website on WordPress safe and secure?
A WordPress site can be very secure, but it’s not automatically safe just because it’s WordPress. Its security depends heavily on how you maintain it.
A secure WordPress site typically includes:
- Regular updates to core, themes, and plugins
- Strong password policies and two-factor authentication
- A properly configured firewall
- HTTPS encryption
- Regular security scans
- A solid backup strategy
Many security breaches happen not because WordPress itself is insecure, but because of outdated software, weak passwords, or missing security layers.
How do I protect my WordPress site?
Security requires a multi-layered approach. Here are some ways to protect your WordPress site:
- Update WordPress core, themes, and plugins promptly, especially for security releases
- Use strong passwords and two-factor authentication
- Install a reputable security plugin with firewall features
- Automate backups with a plugin like Duplicator
- Use HTTPS and make sure your site has a valid SSL certificate
- Remove unused themes and plugins
- Limit admin accounts and login attempts
- Use security-focused hosting
- Check logs, run scans, and stay alert for unusual behavior
No single measure provides complete protection, which is why this layered approach is so important.
Final Thoughts
Setting up proper firewall protection might take a bit of time initially, but it’s far easier than recovering from a hack.
The peace of mind alone makes it worthwhile, knowing your site has that crucial filter between it and the constant barrage of attacks. Plus, a secure WordPress site helps build trust with your visitors and customers.
Remember though, security isn’t a one-and-done task. It’s an ongoing process that requires attention and updates as threats evolve. Think of it as regular maintenance – like changing your car’s oil or getting a health checkup.
And critically, even the best firewall can fail. This is why having reliable, tested backups is the ultimate safety net for your WordPress site. With Duplicator, you can create complete site backups that make recovery from any security incident straightforward and reliable.
Don’t wait until after a breach to realize the value of professional-grade backup protection. Pair your new firewall with Duplicator Pro for the ultimate WordPress security solution!
While you’re here, I think you’ll like these other WordPress guides:

![[New Plugin] Activity Log: Track Every Change, Login, and Action on Your WordPress Site](https://duplicator.com/wp-content/uploads/2026/02/Announcement-Activity-Log.jpg)